Integrating Google Accounts with Auth0 Using Terraform
Now I’m going to add Google Accounts to the growing list of options our users can use with our cross-platform native mobile app. Unforatunetly I looked high and low in the Google Cloud Terraform provider and could not find a way to use Terraform to automate the configuration needed in Google Cloud. I had to use ClickOps.
Manual Configuration in Google Cloud
Despite thorough searching, I couldn’t find a way to configure the necessary Google Cloud settings using Terraform alone. Specifically, there was no Terraform support for the Google OAuth consent screen and OAuth 2.0 client setup. As a result, I had to resort to ClickOps — manual operations in the Google Cloud Console.
First, I manually created a new Google Cloud project. Next, I enabled the People API (people.googleapis.com). Although some documentation suggested enabling the Google+ API, that service has already been deprecated and shut down.
Technically, it would have been possible to automate the creation of the project and API registration using Terraform. However, doing so would require Google Cloud organization-level access to create service accounts and manage projects. Given that this was our sole use case for Google Cloud, I decided to avoid the added complexity of setting up a full Google Cloud organization structure.
Setting Up OAuth Consent
In the Google Cloud Console, I navigated to the API & Services section and selected OAuth consent screen. There, I entered basic branding details such as the application name and support email. I also added auth0.com as an authorized domain.
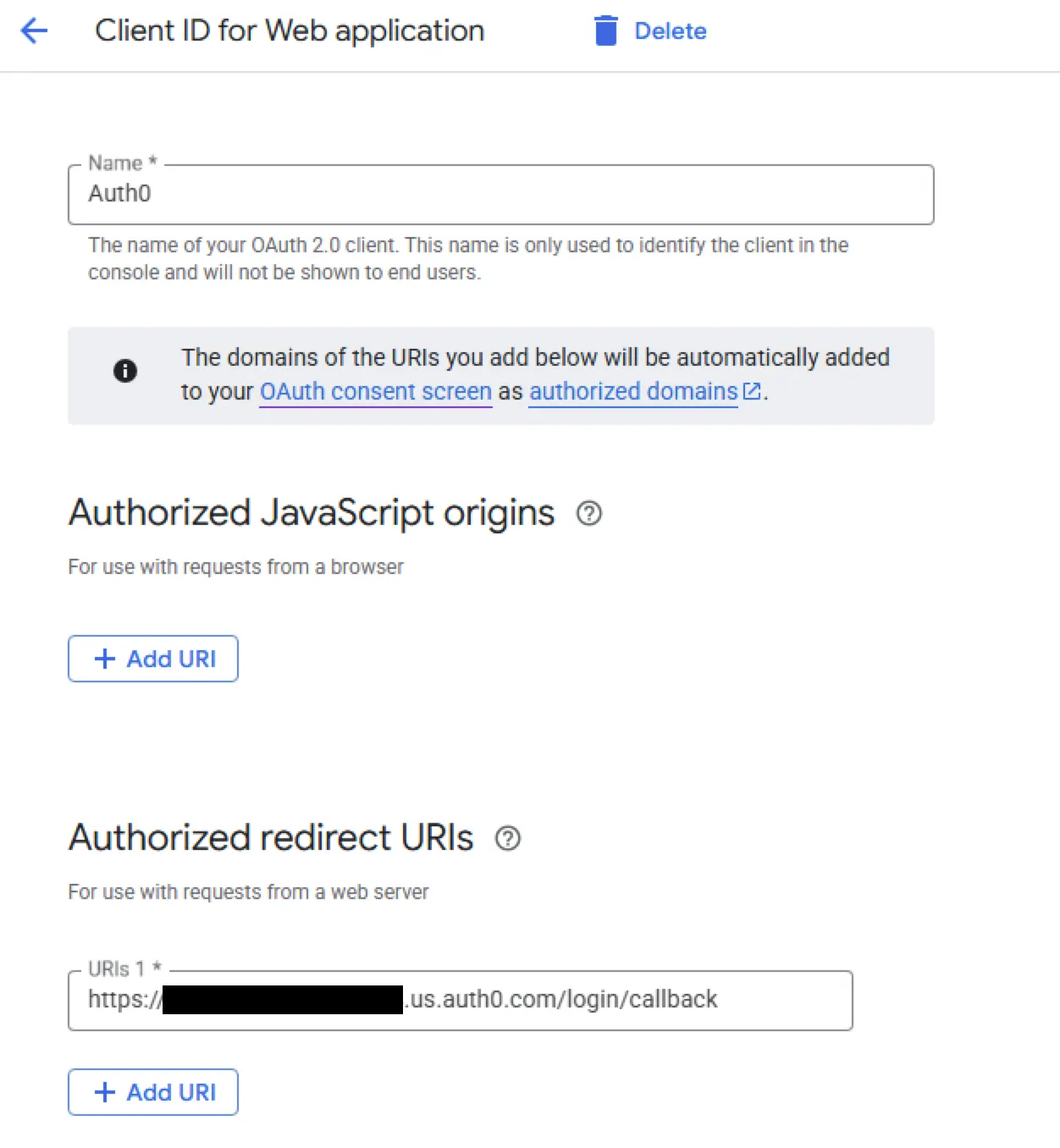
Under the Credentials section, I created a new OAuth 2.0 client ID and subsequently generated a client secret. This manual step was necessary to get the credentials I would later use with Auth0.
Registering with Auth0 Using Terraform
With the Google OAuth credentials in hand, I turned back to Terraform to integrate Google login with Auth0. Unlike our experience with Entra ID, where I could automate most steps using the azuread Terraform provider, the Google setup required capturing values from the manual ClickOps step.
Here is the Terraform code I used to configure the Auth0 connection for Google:
resource "auth0_connection" "google" {
name = "google-oauth2"
strategy = "google-oauth2"
options {
client_id = var.google.client_id
client_secret = var.google.client_secret
scopes = ["profile", "email"]
}
}
The client_id and client_secret values were added to our Terraform configuration as input variables, which I manually populated from the Google Cloud Console. Associating the Connection with the Application
Finally, I linked this new connection to our existing .NET MAUI client application within Auth0. This ensures that users signing in through the app can now choose to authenticate with their Google account:
resource "auth0_connection_clients" "google" {
connection_id = auth0_connection.google.id
enabled_clients = [
auth0_client.maui_app.client_id
]
}
Conclusion
While the integration of Google accounts with Auth0 involved some unavoidable ClickOps, especially on the Google Cloud side, I managed to bring everything else under Terraform’s control. As a result, future updates and maintenance can remain consistent with our Infrastructure-as-Code practices, even if the initial setup required a bit of manual intervention.